Automatic Scanning for Malicious Data: Protecting Your Docly Websites
In today's digital landscape, website security is paramount. This article explores how our automatic scanning works behind the scenes to discover attempts of HTML injection and other malicious data, helping protect Docly websites from potential threats.
The Problem: HTML Injection and XSS Attacks
External visitors to your published Docly websites may submit user input that gets stored in Docly. While most users have good intentions, some may attempt to exploit vulnerabilities.
Consider this example:
<html>
<head>
<title>New Order Notification</title>
</head>
<body>
You have a new order from: #order.Name#
... more information about the order here ...
</body>
</html>This code notifies site admins of new orders. The #order.Name# placeholder is replaced with user-provided information. However, if a malicious user submits a script instead of their name, it could be executed when the admin views the page.
Correct code here would be:
<html>
<head>
<title>New Order Notification</title>
</head>
<body>
You have a new order from: #docly.toHtml(order.Name)#
... more information about the order here ...
</body>
</html>Where the value has been escaped with the docly.toHtml function. Which you need to do with all pure text values you want to display in HTML, also to make sure that it is displayed correctly.
>
Risks of Cross-Site Scripting (XSS)
Allowing users to "inject" (add) to your HTML pages can lead to cross-site scripting (XSS) attacks, which can have severe consequences:
Risk Type | Description | Potential Impact |
|---|---|---|
Data Theft | Attackers can steal sensitive information like login credentials or personal data. | Financial loss, identity theft, privacy breaches |
Session Hijacking | Attackers can take over user sessions, gaining unauthorized access to accounts. | Unauthorized transactions, data manipulation |
Website Defacement | Attackers can alter website content, damaging brand reputation. | Loss of user trust, potential business disruption |
Malware Distribution | XSS can be used to distribute malware to site visitors. | Infection of user devices, further spread of malware |
Phishing Attacks | Attackers can inject fake login forms or misleading content. | User credential theft, financial fraud |
The Solution: Automatic Data Scanning
To mitigate these risks, we've implemented automatic scanning of values when updating Docly documents.
SOLUTION
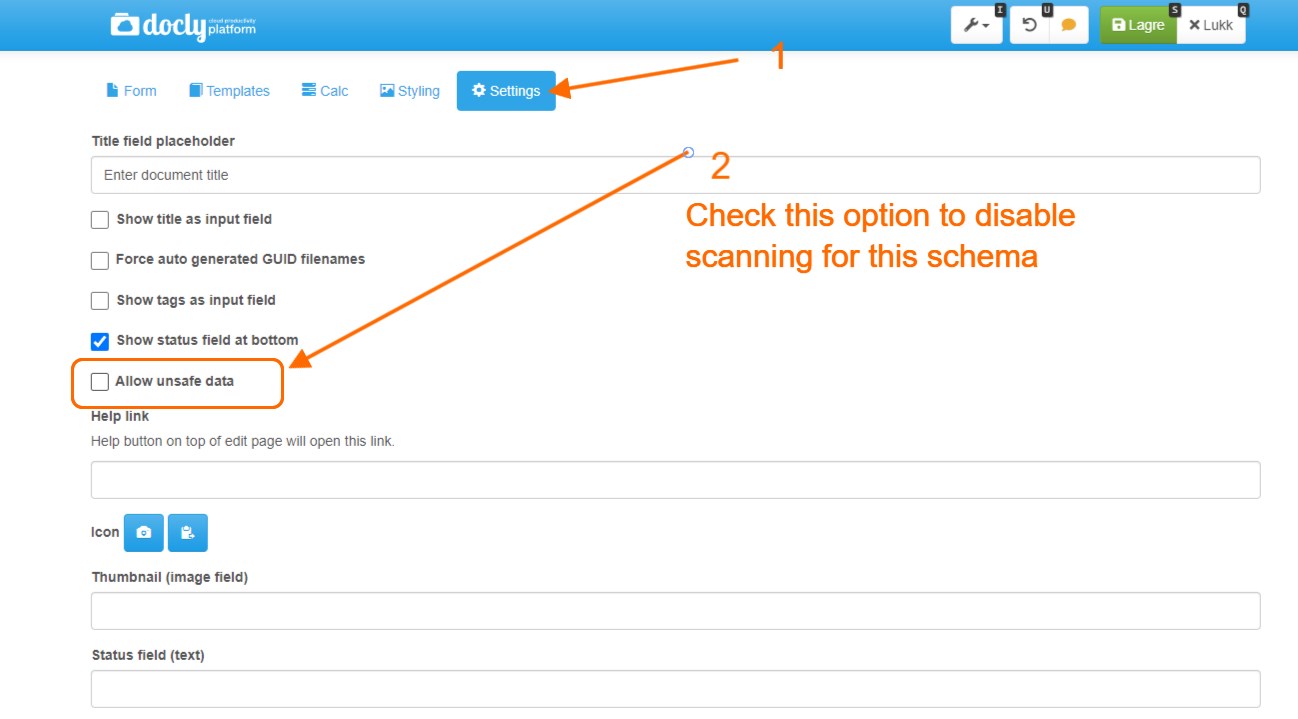
- Do not enable the "Allow unsafe data" data on your schemas.
- Save data using a schema you have setup (don't use SaveJson, as it is less safe)
- Use docly.toHtml() on your templates to display special characters correctly
>
Key Features of Our Scanning Process
Feature | Description | Benefit |
|---|---|---|
Pattern Matching | Advanced algorithms detect suspicious input patterns. | Identifies known attack vectors quickly |
Heuristic Analysis | System learns from past threats to identify new, similar risks. | Adapts to evolving threat landscape |
Regular Updates | Continuous updates to scanning algorithms. | Addresses emerging threats promptly |
Third-Party Integration | Leverages industry-leading security tools. | Enhances detection capabilities |
>
Benefits of Automatic Scanning
Real-time Protection: Threats are identified and neutralized as data is submitted.
Reduced Manual Oversight: Automated processes reduce the need for constant human monitoring.
Improved User Trust: Visitors can interact with your site knowing their data is protected.
>
Related Error Messages
Error message | Description |
|---|---|
Unsafe content detected (ScriptTags) | This error occurs when the system detects script tags in the content, which can be used to execute malicious scripts. |
Unsafe content detected (JavaScriptEvents) | This error occurs when the system detects JavaScript event handlers in the content, which can be used to trigger malicious actions. |
Unsafe content detected (Base64Data) | This error occurs when the system detects Base64 encoded data in the content, which can be used to hide malicious code. |
>
How to disable scanning
Best Practices for Maintaining Security
While automatic scanning is a powerful tool, it's most effective when combined with other security measures:
Practice | Description | Implementation Tips |
|---|---|---|
Input Validation | Verify and sanitize all user inputs server-side. | Always verify user provided data with strict rules with the docly validation functions: |
Output Encoding | Encode user-generated content before display. | Use HTML entity encoding, context-specific encoding: |
Content Security Policy (CSP) | Restrict resource loading and script execution. | Implement strict CSP headers, use nonce-based CSP: |
Regular Security Audits | Periodically review website security measures. | Conduct both automated and manual penetration testing |
User Education | Train team on recognizing and reporting threats. | • Take some time and read/learn about the possible threats. |
Conclusion
Automatic scanning for malicious data is a crucial line of defense in web application security. By proactively identifying and mitigating threats, we protect both your website and its users from potential harm.
Remember, security is an ongoing process. Stay informed about the latest threats and continuously update your defenses to maintain a secure online environment.